Vulnerability Management(Nessus)
Welcome to the vulnerability management lab! In this lab, I will be using Nessus to identify and prioritize vulnerabilities within the Virtual machine. Nessus is a powerful vulnerability scanner that allows us to scan our network and systems for known vulnerabilities, misconfigurations, and other weaknesses that could potentially be exploited by malicious actors.
In this lab, I set up Nessus Essentials, installed Windows 10 inside a virtual machine using VMware Workstation Player, added some outdated software, and performed vulnerability checks on the virtual machine to look for any potential security flaws. Later, I make an effort to fix some of the flaws.
I first start by downloading, Vmware Workstation, a windows 10 iso and Nessus.
It is crucial to set the network adapter to bridged while constructing the Windows virtual machine. It connects the virtual machine to the physical computer's network so that Nessus can communicate with the virtual machine effortlessly.
I could perform my first scan on the machine
to see if it was working correctly.
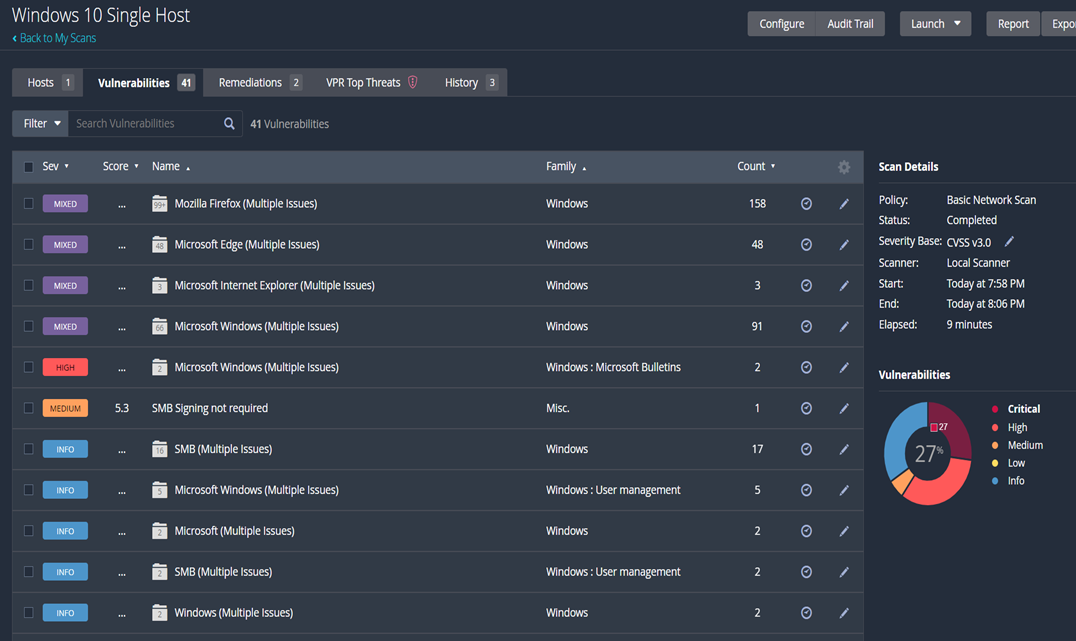
According to the basic vulnerability scan, there appear to be 18 vulnerabilities. Since I did not supply any credentials, most of them are info and low vulnerabilities, but if I do, the scan will be more thorough and may uncover additional information and problems.
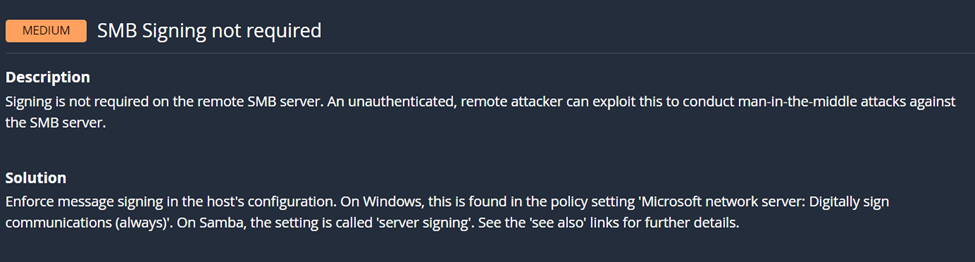
By clicking on the vulnerability, I can see more details about it and even some recommended solutions by the system on how to remediate it.
There are other vulnerabilities such as Trace route information which from my research it means that the host accepts ICMP, and trace route information can be seen. This is not necessarily a vulnerability but something to be aware of.
The virtual computer will next be configured such that it can receive authorized scans, after which I will give Nessus my login information and attempt a new scan in order to compare the results.
Activating the remote registry in services.msc is what Nessus advises doing in order to do authorized scans on window hosts that are not part of the domain. This enables the scanner to access the registry and search for unsafe configurations. Next, make sure that file and printer sharing is enabled.
Then I went to user Account control Settings and set
it to never notify. This is not recommended on an actual corporate computer but
since the computer is not on the domain I have to use this to able to scan it.
Lastly I had to go to the registry editor, then I went into HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System. In this folder, I create a 32-bit DWORD called LocalAccountTokenFilterPolicy and set the hex data value to 1 and then restart the Virtual machine.At this point I am ready to rescan the computer but with credentials.
I am now expecting more result with this scan since
the scanner now has credentials so its able to enter the computer and dive
deeper to find more vulnerabilities.
Now before I go about remediating any of the issues I
will first install an older version of Firefox and do a rescan once again. The
new scan should discover a lot more vulnerabilities with the old version of
Firefox.
To install a deprecated version of Firefox on the VM,
follow these steps:
- Download
the deprecated version of Firefox from the Mozilla FTP server (https://ftp.mozilla.org/pub/firefox/releases/).
- On the VM, open the downloaded Firefox installer and follow the prompts to complete the installation process.
From this lab, I have gathered that one of the primary
benefits of Nessus is its ability to identify a wide range of vulnerabilities
across different platforms and technologies. Whether you are running a Windows
or Linux environment, Nessus can scan your systems and identify vulnerabilities
such as missing patches, weak passwords, and misconfigured services. By
regularly conducting scans with Nessus, you can ensure that you are aware of
the vulnerabilities present in your systems and can take steps to mitigate them
before they can be exploited by attackers.
In conclusion, Nessus is a powerful and feature-rich
tool for performing vulnerability assessments and identifying security
weaknesses in a network. By regularly scanning systems and analyzing
the results, one can identify and prioritize vulnerabilities and take steps to
mitigate them before they can be exploited by attackers.
Using Nessus can help improve an organization's
security posture, reduce the risk of data breaches, and demonstrate compliance
with regulatory requirements. With its wide range of scanning capabilities and
customizable options, Nessus is a valuable asset for any security professional.












Comments
Post a Comment