Practitioner Lab 1: File path traversal, traversal sequences blocked with absolute path bypass
This lab contains a path traversal vulnerability in the display of product images.
The application blocks traversal sequences but treats the supplied filename as being relative to a default working directory.
To solve the lab, retrieve the contents of the /etc/passwd file.
I began by looking into one of these pages which have images
I then went into the source code and took a look at where the image was being accessed
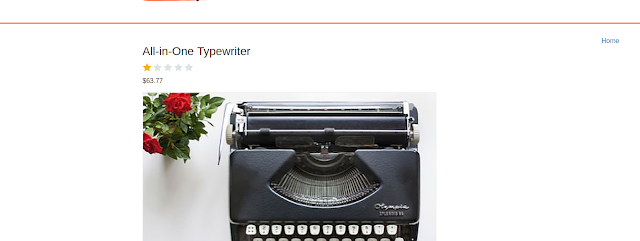
I then went into it and changed the image for the absolute path of the file /etc/passwd
This then resulted in the lab being finished.
To solve this using Burp I went into the http history and this allowed me to see the request for images.
Here I take a look at the request and then change it to the absolute path of /etc/passwd and then I get the contents of the file





Comments
Post a Comment