Active Directory Pentesting Lab
This is my Pentesting active directory lab. I already have a simple AD lab which I used to learn how active directory works but this one I will use to attack it and to try and exploit some vulnerabilities and misconfigurations.
I Started by installing Windows Server 2022 as well as a Windows 10 Vm.
This Windows Server 2022 will act as my Domain Controller
which is the server that runs the active directory services.
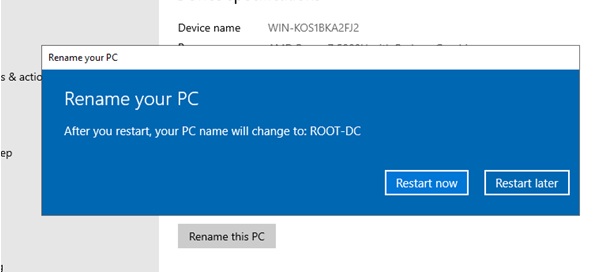
The first thing I did was change the name of
my Windows server machine to something that I would remember. In this case, it's named ROOT-DC.
I then went to manage and added “roles and features”
I made sure to add Active Directory Domain Services which is
also known as Active Directory Data store.
After installing everything I went and promoted my server to
be a domain controller. I had to add a new forest because I don’t have an
existing domain nor to do I have an existing forest.
I named it Root_Lab.local
Here is the NTDS this file is very important.
NTDS.dit stands for new technology directory services directory information tree. This file stores all the data of the active directory. This includes the hashes, users, computers, groups as well as security descriptors.
GPO’s which are group policy objects are distributed to the network via a network share called SYSVOL. As can be seen, this is stored on the domain controller.
Now that everything was set up properly I can login with the
admin account for this domain.
Now the next step is for me to set up certificate services.
This is because I want to try and attack this machine later and this will be
required.
To do this is the same way I added the AD DS but in this
case, I would add certificate services instead of the Data store.
Certificate services are used to verify identities in a domain
controller. In simple it is extra security that it is usually on in most
businesses. It allows me to use LDAP and secure LDAPS. LDAP is port 389 and
LDAPS is port 636 which is LDAP over SLL
There are quite a few attacks that are related to Active Directory Certificate Services and I would like to try them to learn from them.
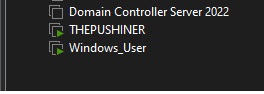
After this, I set up 2 Windows machines with different names.
These machines were integrated into the domain and I also renamed them to be able to better identify which machines they are.
Now I will start to manage the users and computers. I will
also start to add them to different OU’s so that I can apply policies to them
better.
I made a new organizational unit to keep the users separated.
Now the only accounts in users are the Admin account and the guest account which is disabled.
Now I will create some more accounts.
I purposely made 2 accounts that shouldn’t be made. One of
them is another Administrator account and the second one is a SQL service
account but instead of having the needed privileges I am giving it admin privilege.
Another thing that I did was to give it a password that meets the standards of
passwords with uppercase, lowercase, numbers, and symbols as well as more
than 8 characters but this password can
be easily broken.
I also added this in the description because as far as I know, it is a common occurrence that domain admins tend to do.
Here I made some other low-level accounts to be part of the user group.
I am purposely keeping the admin users with normal users because this is a common misconfiguration that is often seen and I want to try and exploit it.
My next step is to make a file share that I can later use to
hack into the system.
I made a new share called hackme which I will use at a later
time to hack into the system. Most likely I will be trying to do an LLMNR poisoning.
Here I added an SPN to my SQL Service. SPN is a unique
identifier for services in the active directory.
After querying the system for the service It can be seen
that SQL.Service is there.
Now the final thing I need to do is set up a group policy
This group policy I will push for the entire domain.
This GPO will be to disable Windows Defender this way I can
easily run the attacks without having to worry about the attacks being stopped.
Now I set up my ip as static because I didn’t want it to change.
Lastly, now I need to add the machines to the domain. The
first thing I did was go to the network settings and add the domain controller's IP to the DNS server.
I did this for both machines.
Now the computers have fully joined the domain.
By going into my domain controller, tools and “Active Directory
Users and Computers” I can check in the
computers' OU to see if the computers are really there. This is because every time a computer joins the domain they go into that OU by default.
Now I log back into the machines to change a few settings
that will be needed for me to do my attacks later.
The first is in “edit local users and groups”
I enabled this account
In a best practice, you would want this account disabled but
in this case, I want it to be able to attack the active directory.
This is also often on at most places. It shouldn’t but it is
a common thing that occurs.
I checked if my network discovery was on. Since it wasn’t I turned it on.
Lastly, I configured it so that my network share could be
accessed with another account which was the administrator account.























Comments
Post a Comment