Lab 11: Remote code execution via web shell upload
This lab contains a vulnerable image upload function. It doesn't perform any validation on the files users upload before storing them on the server's filesystem.
I have to upload a basic PHP web shell and use it to exfiltrate the contents of the file /home/carlos/secret
The first step is to log in with the account I was provided
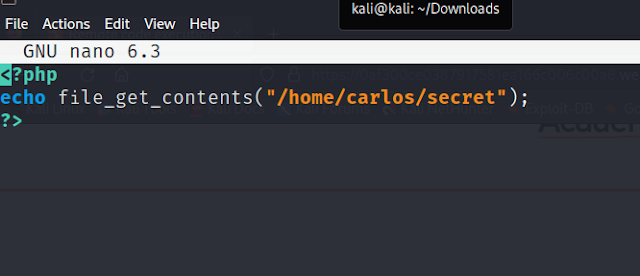
I found a PHP line to get the file contents
I put it into a PHP file and now I am going to upload this file to then be able to get the contents of the file
After I uploaded the file I then sent a GET request to the file path
This gave me the final flag







Comments
Post a Comment