Practitioner Lab 3: File path traversal, traversal sequences stripped with superfluous URL-decode
This lab contains a path traversal vulnerability in the display of product images.
The application blocks input containing path traversal sequences. It then performs a URL-decode of the input before using it.
To solve the lab, retrieve the contents of the /etc/passwd file.
I started by looking around the page to see how it worked.
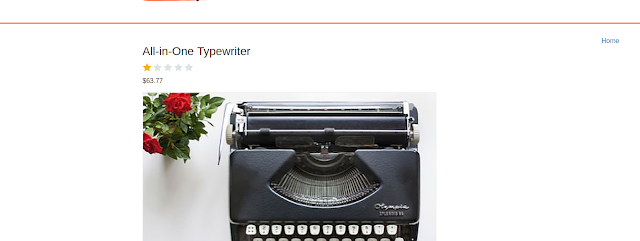
I then opened one of the images to see the request.
I looked at the request and then I changed it
I had to encode it for it to work.
and the lab is solved.





Comments
Post a Comment