Practitioner Lab 6: SSRF with blacklist-based input filter
Practitioner Lab 6: SSRF with blacklist-based input filter
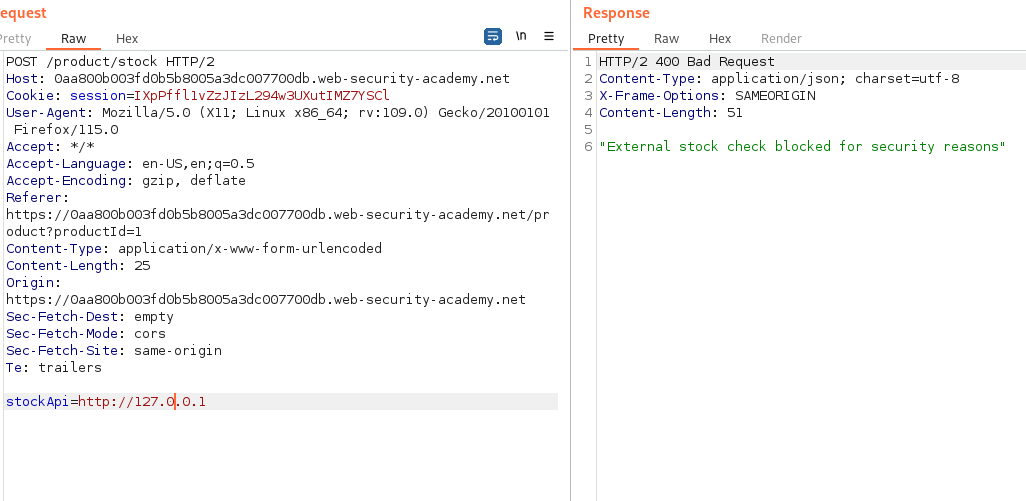
I start by looking at the website itself and try to find if its communicating with the backend
In this case it does this inside of the items they are selling to check if there are any items in stock
Now I will take a look at the request to see how it is working
Here is the stock API which I can use to send request to the backend
I tried to access the /admin page using the trust of the localhost but it is blocked.
It tells me that External stock check blocked for security reasons.
Now There are a few things I can do and I will try to do all the options I know
I tried using 127.1 instead of 127.0.0.1 but it didn’t work. I also tried to URL encode it but it also didn’t work
After trial and error, I found a solution to the problem
If I used simply the loopback it would be blocked.
But if I used 127.1 it would pass meaning that it wasn’t only blacklisting the localhost but it was also blacklisting the admin word
so I tried encoding the word admin but it didn’t work. Because of this I used double encoding to do it.
This got me closer but if i double encode the whole word it doesn’t fully work so what if I encode only part of the word
here i encoded the a
Here I also double encoded the a with URL enconding. This worked.
Now I captured the request to delete to add it to the original request
/admin/delete?username=carlos











Comments
Post a Comment